The recent mass-theft of authentication tokens from Salesloft, whose AI chatbot is used by a broad swath of corporate America to convert customer interaction into Salesforce leads, has left many companies racing to invalidate the stolen credentials before hackers can exploit them. Now Google warns the breach goes far beyond access to Salesforce data, noting the hackers responsible also stole valid authentication tokens for hundreds of online services that customers can integrate with Salesloft, including Slack, Google Workspace, Amazon S3, Microsoft Azure, and OpenAI.

Salesloft says its products are trusted by 5,000+ customers. Some of the bigger names are visible on the company’s homepage.
Salesloft disclosed on August 20 that, “Today, we detected a security issue in the Drift application,” referring to the technology that powers an AI chatbot used by so many corporate websites. The alert urged customers to re-authenticate the connection between the Drift and Salesforce apps to invalidate their existing authentication tokens, but it said nothing then to indicate those tokens had already been stolen.
On August 26, the Google Threat Intelligence Group (GTIG) warned that unidentified hackers tracked as UNC6395 used the access tokens stolen from Salesloft to siphon large amounts of data from numerous corporate Salesforce instances. Google said the data theft began as early as Aug. 8, 2025 and lasted through at least Aug. 18, 2025, and that the incident did not involve any vulnerability in the Salesforce platform.
Google said the attackers have been sifting through the massive data haul for credential materials such as AWS keys, VPN credentials, and credentials to the cloud storage provider Snowflake.
“If successful, the right credentials could allow them to further compromise victim and client environments, as well as pivot to the victim’s clients or partner environments,” the GTIG report stated.
The GTIG updated its advisory on August 28 to acknowledge the attackers used the stolen tokens to access email from “a very small number of Google Workspace accounts” that were specially configured to integrate with Salesloft. More importantly, it warned organizations to immediately invalidate all tokens stored in or connected to their Salesloft integrations — regardless of the third-party service in question.
“Given GTIG’s observations of data exfiltration associated with the campaign, organizations using Salesloft Drift to integrate with third-party platforms (including but not limited to Salesforce) should consider their data compromised and are urged to take immediate remediation steps,” Google advised.
On August 28, Salesforce blocked Drift from integrating with its platform, and with its productivity platforms Slack and Pardot.
The Salesloft incident comes on the heels of a broad social engineering campaign that used voice phishing to trick targets into connecting a malicious app to their organization’s Salesforce portal. That campaign led to data breaches and extortion attacks affecting a number of companies including Adidas, Allianz Life and Qantas.
On August 5, Google disclosed that one of its corporate Salesforce instances was compromised by the attackers, which the GTIG has dubbed UNC6040 (“UNC” stands for “uncategorized threat group”). Google said the extortionists consistently claimed to be the threat group ShinyHunters, and that the group appeared to be preparing to escalate its extortion attacks by launching a data leak site.
ShinyHunters is an amorphous threat group known for using social engineering to break into cloud platforms and third-party IT providers, and for posting dozens of stolen databases to cybercrime communities like the now-defunct Breachforums.
The ShinyHunters brand dates back to 2020, and the group has been credited with or taken responsibility for dozens of data leaks that exposed hundreds of millions of breached records. The group’s member roster is thought to be somewhat fluid, drawing mainly from active denizens of the Com, a mostly English-language cybercrime community scattered across an ocean of Telegram and Discord servers.
Recorded Future’s Alan Liska told Bleeping Computer that the overlap in the “tools, techniques and procedures” used by ShinyHunters and the Scattered Spider extortion group likely indicate some crossover between the two groups.
To muddy the waters even further, on August 28 a Telegram channel that now has nearly 40,000 subscribers was launched under the intentionally confusing banner “Scattered LAPSUS$ Hunters 4.0,” wherein participants have repeatedly claimed responsibility for the Salesloft hack without actually sharing any details to prove their claims.
The Telegram group has been trying to attract media attention by threatening security researchers at Google and other firms. It also is using the channel’s sudden popularity to promote a new cybercrime forum called “Breachstars,” which they claim will soon host data stolen from victim companies who refuse to negotiate a ransom payment.
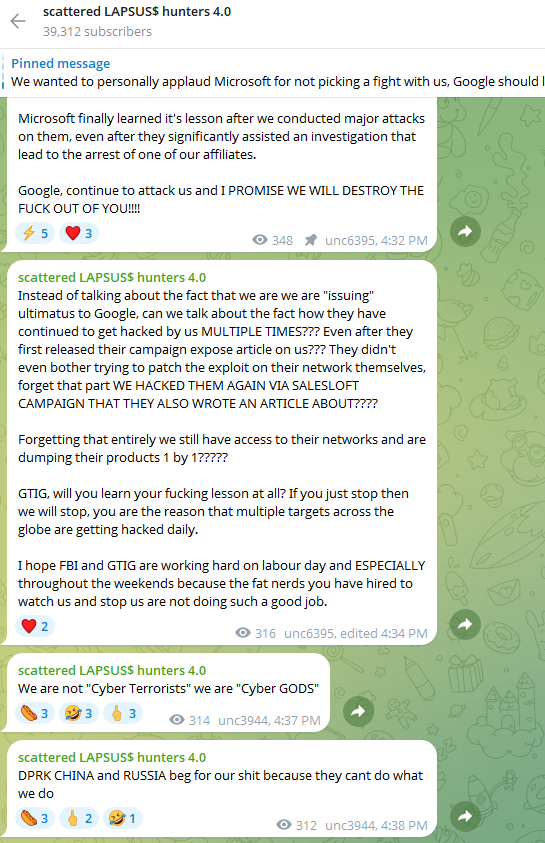
The “Scattered Lapsus$ Hunters 4.0” channel on Telegram now has roughly 40,000 subscribers.
But Austin Larsen, a principal threat analyst at Google’s threat intelligence group, said there is no compelling evidence to attribute the Salesloft activity to ShinyHunters or to other known groups at this time.
“Their understanding of the incident seems to come from public reporting alone,” Larsen told KrebsOnSecurity, referring to the most active participants in the Scattered LAPSUS$ Hunters 4.0 Telegram channel.
Joshua Wright, a senior technical director at Counter Hack, is credited with coining the term “authorization sprawl” to describe one key reason that social engineering attacks from groups like Scattered Spider and ShinyHunters so often succeed: They abuse legitimate user access tokens to move seamlessly between on-premises and cloud systems.
Wright said this type of attack chain often goes undetected because the attacker sticks to the resources and access already allocated to the user.
“Instead of the conventional chain of initial access, privilege escalation and endpoint bypass, these threat actors are using centralized identity platforms that offer single sign-on (SSO) and integrated authentication and authorization schemes,” Wright wrote in a June 2025 column. “Rather than creating custom malware, attackers use the resources already available to them as authorized users.”
It remains unclear exactly how the attackers gained access to all Salesloft Drift authentication tokens. Salesloft announced on August 27 that it hired Mandiant, Google Cloud’s incident response division, to investigate the root cause(s).
“We are working with Salesloft Drift to investigate the root cause of what occurred and then it’ll be up to them to publish that,” Mandiant Consulting CTO Charles Carmakal told Cyberscoop. “There will be a lot more tomorrow, and the next day, and the next day.”

How do hackers hack phones? In several ways. But also, there are several ways you can prevent it from happening to you. The thing is that our phones are like little treasure chests. They’re loaded with plenty of personal data, and we use them to shop, bank, and take care of other personal and financial matters—all of which are of high value to identity thieves. However, you can protect yourself and your phone by knowing what to look out for and by taking a few simple steps. Let’s break it down by first understanding what phone hacking is, taking a look at some common attacks, and learning how you can prevent it.
Phone hacking refers to any method where an unauthorized third party gains access to your smartphone and its data. This isn’t just one single technique; it covers a wide range of cybercrimes. A phone hack can happen through software vulnerabilities, like the spyware campaigns throughout the years that could monitor calls and messages. It can also occur over unsecured networks, such as a hacker intercepting your data on public Wi-Fi. Sometimes, it’s as simple as physical access, where someone installs tracking software on an unattended device.
Hackers have multiple avenues of attacking your phone. Among these common methods are using malicious apps disguised as legitimate software, exploiting the vulnerabilities of unsecure public Wi-Fi networks, or deploying sophisticated zero-click exploits that require no interaction from you at all. The most common method, however, remains social engineering, where they trick you into giving them access. Let’s further explore these common hacking techniques below.
Whether hackers sneak it onto your phone by physically accessing your phone or by tricking you into installing it via a phony app, a sketchy website, or a phishing attack, hacking software can create problems for you in a couple of ways:
Some possible signs of hacking software on your phone include:
In all, hacking software can eat up system resources, create conflicts with other apps, and use your data or internet connection to pass your personal information into the hands of hackers.
This classic form of attack has been leveled at our computers for years. Phishing is where hackers impersonate a company or trusted individual to get access to your accounts or personal info or both. These attacks take many forms such as emails, texts, instant messages, and so forth, some of which can look really legitimate. Common to them are links to bogus sites that attempt to trick you into handing over personal info or that install malware to wreak havoc on your device or likewise steal information. Learning to spot a phishing attack is one way to keep yourself from falling victim to one.
Professional hackers can use dedicated technologies that search for vulnerable mobile devices with an open Bluetooth connection. Hackers can pull off these attacks when they are within range of your phone, up to 30 feet away, usually in a populated area. When hackers make a Bluetooth connection to your phone, they might access your data and info, yet that data and info must be downloaded while the phone is within range. This is a more sophisticated attack given the effort and technology involved.
In August of 2019, then CEO of Twitter had his phone hacked by SIM card swapping scam. In this type of scam, a hacker contacts your phone provider, pretends to be you, then asks for a replacement SIM card. Once the provider sends the new SIM to the hacker, the old SIM card is deactivated, and your phone number will be effectively stolen. This enables the hacker to take control of your phone calls, messages, among others. The task of impersonating someone else seems difficult, yet it happened to the CEO of a major tech company, underscoring the importance of protecting your personal info and identity online to prevent hackers from pulling off this and other crimes.
While a phone call itself cannot typically install malware on your device, it is a primary tool for social engineering, known as vishing or voice phishing. A hacker might call, impersonating your bank or tech support company, and trick you into revealing sensitive information like passwords or financial details. They might also try to convince you to install a malicious app. Another common tactic is the “one-ring” scam, where they hang up hoping you’ll call back a premium-rate number. To stay safe, be wary of unsolicited calls, never provide personal data, block suspicious numbers, and check that your call forwarding isn’t enabled.
Generally, a phone that is powered off is a difficult target for remote hackers. However, modern smartphones aren’t always truly off. Features like Apple’s Find My network can operate in a low-power mode, keeping certain radios active. Furthermore, if a device has been previously compromised with sophisticated firmware-level malware, it could activate upon startup. The more common risk involves data that was already stolen before the phone was turned off or if the device is physically stolen. While it’s an uncommon scenario, the only sure way to take a device offline and completely sever all power is by removing the battery, where possible.
Hacking a phone’s camera is referred to as camfecting, usually done through malware or spyware hidden within a rogue application. Once installed, these apps can gain unauthorized permission to access your camera and record video or capture images without your knowledge. Occasionally, vulnerabilities in a phone’s operating system (OS) have been discovered that could allow for this, though these are rare and usually patched quickly. Protect yourself by regularly reviewing app permissions in your phone’s settings—for both iOS and Android—and revoking camera access for any app that doesn’t absolutely need it. Always keep your OS and apps updated to the latest versions.
This is a long-standing debate with no simple answer. iPhones are generally considered more secure due to Apple’s walled garden approach: a closed ecosystem, a strict vetting process for the App Store, and timely security updates for all supported devices. Android’s open-source nature offers more flexibility but also creates a more fragmented ecosystem, where security updates can be delayed depending on the device manufacturer. However, both platforms use powerful security features like application sandboxing.
The most important factor is not the brand but your behavior. A user who practices good digital hygiene—using strong passwords, avoiding suspicious links, and vetting apps—is well-protected on any platform.
Detecting a phone hack early can save you from significant trouble. Watch for key red flags: your battery draining much faster than usual, unexpected spikes in your mobile data usage, a persistently hot device even when idle, or a sudden barrage of pop-up ads. You might also notice apps you don’t remember installing or find that your phone is running unusually slow. To check, go into your settings to review your battery and data usage reports for any strange activity. The most effective step you can take is to install a comprehensive security app, like McAfee® Mobile Security, to run an immediate scan and detect any threats.
Discovering that your phone has been hacked can be alarming, but acting quickly can help you regain control and protect your personal information. Here are the urgent steps to take so you can remove the hacker, secure your accounts, and prevent future intrusions.
While there are several ways a hacker can get into your phone and steal personal and critical information, here are a few tips to keep that from happening:
Your smartphone is central to your life, so protecting it is essential. Ultimately, your proactive security habits are your strongest defense against mobile hacking. Make a habit of keeping your operating system and apps updated, be cautious about the links you click and the networks you join, and use a comprehensive security solution like McAfee® Mobile Security.
By staying vigilant and informed, you can enjoy all the benefits of your mobile device with confidence and peace of mind. Stay tuned to McAfee for the latest on how to protect your digital world from emerging threats.
The post How Do Hackers Hack Phones and How Can I Prevent It? appeared first on McAfee Blog.